網路攻防可說是日新月異,以前我們認為加密便能保護資料避免被中間人窺探我的信用卡、帳號密碼。變態的駭客為了一覽無疑敏感資料而不擇手段,而誕生SSL剝離攻擊。
在SSL剝離攻擊的角色,用戶角度,駭客扮演服務器、服務器角度,駭客扮演用戶端。駭客在連線的中間提供proxy功能,所以它不需要任何強大的解密工具去破壞加密封包。
當然加密資料仍是必需的,同理,駭客也能躲在加密連線內,趁你看不到卻偷看你;這是抖音上的有趣視頻
https://www.douyin.com/video/7086153027664497957

在新世代防火牆等資安設備,應支持類似SSL / TLS proxy的功能,或許各家廠商有不同的技術命名。總之此技術能檢查加密流量。
接著我將示範如何用PaloAlto實現TLS proxy,拓樸如下

PA v10.1.3
1)介面management連接MIS、ethernet1/1(PPPoE)連接Internet、ethernet1/2(10.0.0.254)連接Windows 11虛擬機(10.0.0.1)

2)設定安全規則,防火牆允許win11存取網際網路。
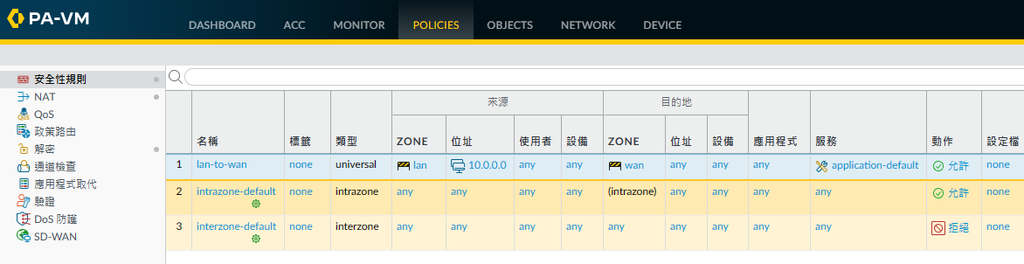
3)設定NAT,win11能透過防火牆轉址。

4)設定設備憑證,這裡的重要觀念,信任憑證如FB、Youtube、抖音等網站,通常都會勾;如未勾「轉送不信任憑證」,當你嘗試用https連接自己的設備,就會被防火牆拒絕連線。

5)設定解密物件,這步驟是可選的,因為PA的解密物件「default」,SSL協定版本上限是2.0,我想更安全於是調整最大(目前為TLS 1.3),其他值都預設不動。

6)設定解密規則,做完就可以提交了。

7)匯出設備憑證,標準做法是MIS透過管理網路下載憑證,再放NAS供用戶電腦要求安裝憑證。
從防火牆對LAN開https供用戶電腦登入設備自行下載也行,但不建議,因為
[1]太危險,非IT員工不應有權限存取防火牆
[2]增加MIS麻煩,你確定非IT員工聽得懂你的要求嗎? 提供越簡單方便的操作越好,通常公用電腦分配給員工使用前,已完成憑證安裝作業了。

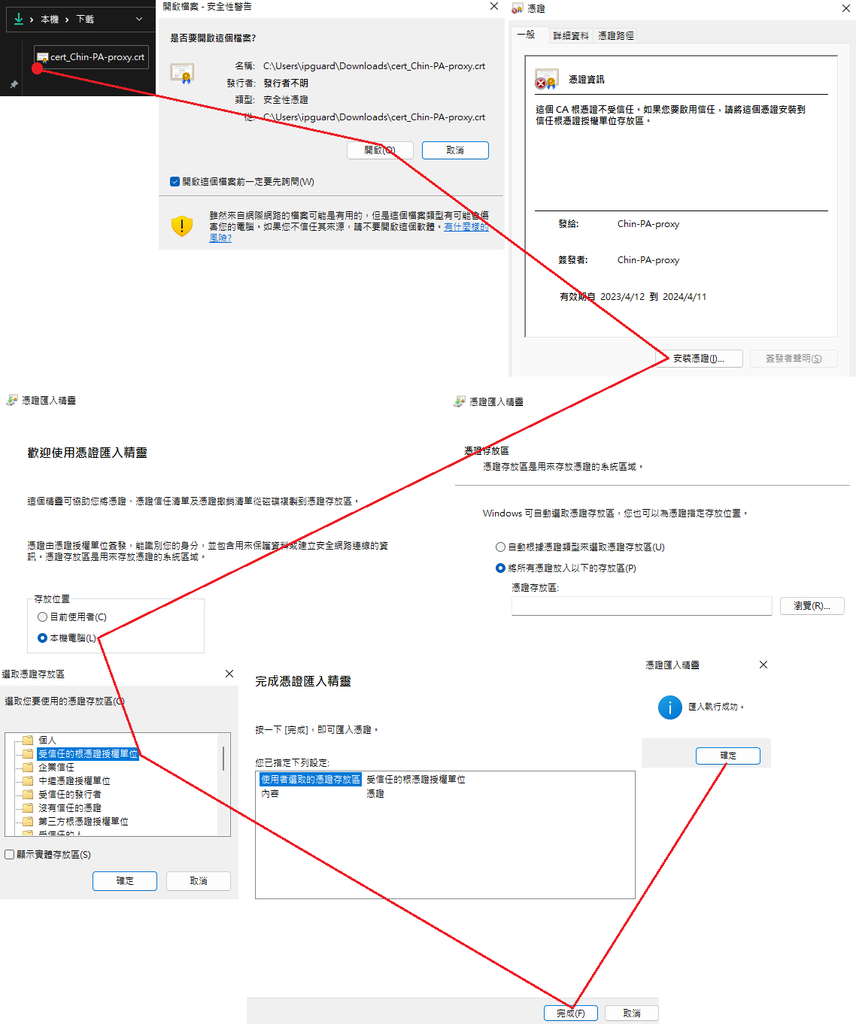
8-1)完成,證明方法是用戶電腦訪問網站時檢視憑證,像我這樣。

8-2)從防火牆可見代理哪些流量。

8-3)在Windows輸入「certmgr.msc」打開憑證存放空間,可檢視這台電腦存放那些憑證。

若你的發行者沒變化,請先檢查你的預設閘道是防火牆。以上步驟與確實安裝憑證。或清除瀏覽資料、改變搜尋引擎。或受到HSTS(HTTP Strict Transport Security)影響。
Network attack & defense that is ever-changing. In the past, we think to crypto data that can protect my info, such as credit-card, password. However, hacker is cunning, so created SSL peel-off attack.
The roles in SSL peel-off attack. For client, hacker acted server. For server, hacker acted client. Hacker provides proxy feature in middle. So hacker is not need any stronger decrypt tool to crack packet(s).
Of course, we are still need to crypto data, but hacker can hide in encrypted connection also. It is funny video on Tiktok.
https://www.douyin.com/video/7086153027664497957
[tiktok]
NG-firewall or security device, they maybe support like SSL / TLS proxy feature. Maybe there are difference named by venders. The key content is that can detect encrypted traffic.
And then, I will demo how setting TLS proxy on PaloAlto, follow topology
[topology]
PA v10.1.3
1) The management interface is connect MIS, ethernet1/1(PPPoE) is connect the Internet, ethernet1/2(10.0.0.254) is connect VM win11(10.0.0.1)
[image]
2)Setting security policy, firewall permit the win11 access the Internet.
[image]
3)Setting NAT, win11 can translate address over firewall.
[image]
4)Setting device certificate. This is important concept, trust certificate are like FB, Youtube, Tiktok website and so on, it is tick usually.
If not yet tick「forward untrust certificate」, when you try connect your device over https, firewall will reject your connection.
[image]
5)Setting decrypt object, this step is optional. The reason is the decrypt object 「default」, its SSL protocol version limit is 2.0 . But I want to more secure, so I create new decrypt object, and SSL protocol version is max(it is TLS 1.3 currently), and other variable is not change.
[image]
6)Setting decrypt rule, and then you can commit.
[image]
7)Export device certificate, standard method that is MIS download it over management network. And upload to NAS, provide clients computer and install.
If you open https on firewall LAN, let client(s) to download certificate self, it is feasible but not suggest. Because
[1]It is so dangerous, non-IT employee(s) should not have permission to access firewall.
[2]It is increase MIS trouble, are you sure your colleague(s) can understand your requirement? So it should simple.
[image]
8-1)Finished, when client(s) access the Internet, you can check the certificate on browser, like me.
[image]
8-2)I can see what proxy traffic on firewall.
[image]
If your issuer is not change, please check your default gateway is firewall. And above steps and install certificate. Or clear surfing data, change search engine. Or you got effect HSTS(HTTP Strict Transport Security).




 留言列表
留言列表


