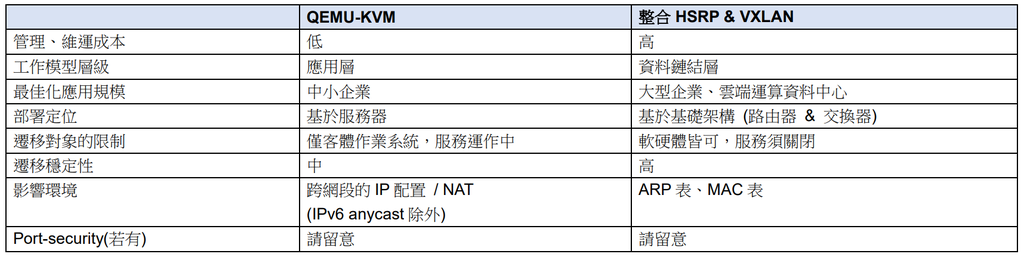
本文適用高階網管!末學先與您逐一複習HSRP、VXLAN、虛擬化動態遷移等技術,並列表其特性。
由思科研發的閘道備援技術,透過路由器加入特定組播,物理上有多個廣域網路出口,邏輯上對終端電腦僅有一個廣域網路出口。平時只有一台路由器做實際的轉發封包行為,當它死了,就會被另一台路由器接管轉發封包的權力,期望將災害復原時間縮到最短。
雖然是L2技術,但它使用UDP實現擴充版VLAN,主要應用在大型資料中心的基礎架構。部署VXLAN,允許位於多處的資料中心使用一個相同的網段分配給主機群。
[拓樸 & 配置]
[VXLAN封包]
虛擬化動態遷移
即遷移運行中的主機,並期望運行中繼續提供服務或資源存取。在此僅介紹QEMU-KVM,它是虛擬化軟體,類似軟體還有Oracle的vm virtualbox、VMware的workstation player,最讓人熟悉的就是利用這些軟體來玩虛擬機器,術語定義,你的物理主機為host OS、而虛擬機為guest OS。你可以在虛擬機安裝多樣類型的作業系統,玩壞都沒關係,也常被工程師用來做實驗,例如軟體、病毒、系統資源等測試。
遷移的準備,在兩部主機上安裝QEMU-KVM,並用其建立容器(container)與安裝或匯入guest OS。並與對等體建立QEMU-KVM連線。
[我的主機是mint18。本機與10.1.1.18建立QEMU-KVM連線,並運行guest OS名為vm]

圖形化的操作比較簡單就不詳述步驟,指令操作如下
apt-get install qemu-kvm libvirt-bin ubuntu-vm-builder bridge-utils virt-manager python-spice-client-gtk qemu-utils spice-vdagent ssh
安裝QEMU-KVM所需套件。補充:可以使用apt-get install cpu-checker 安裝CPU檢查程式,再用指令kvm-ok檢查主機是否支援KVM。
virt-install --name vm --ram 1024 --vcpus 1 --cdrom /var/lib/libvirt/images/CorePlus-current.iso --disk /var/lib/libvirt/images/vm.qcow2,device=disk,bus=sata,format=qcow2,size=0.1
安裝虛擬機器與配置參數
virsh [start / reboot / shutdown / destroy] vm
開機 / 重啟 / 關機 / 強制關機該虛擬機器
virsh connect qemu+ssh://[username]@10.1.1.18/system
與對等體連線,QEMU-KVM連線機制使用round-robin,就是固定時間(通常是幾秒)詢問彼此是否還活著。
遷移的條件有三,(1)QEMU-KVM連線方法使用SSH,這裡的SSH不是遠端登入,而是做為連線通道。
(2)對兩個對等體而言,遷移客體需要相同的容器名稱,容器大小可不同,但是要大於客體空間。
(3)遷移的兩對等體,目錄位置必須相同,如果guest儲存在本機的/var/lib/libvirt/images/,遷移到目的地主機的目錄也必須是/var/lib/libvirt/images/。
[遷移客體中]

遷移的時間取決於對等體間的網路品質與客體大小(就如同傳輸檔案,檔案越大傳輸越久)。「遷移虛擬機」視窗有一「位址」欄位,可以是hostname,但是需要先在本機名稱解析檔(/etc/hosts)加入hostname或你的DNS服務器找得到它。
virsh migrate --persistent --undefinesource tiny qemu+ssh://[username]@10.1.1.18/system
遷移客體到目的地
以上是簡介QEMU-KVM動態遷移虛擬機的說明,不過筆者感到它有幾個缺點,一是連線品質做得不好,容易逾時(即使是直連)。二是上面所述遷移條件之三,有關遷移的目錄位置(兩端必須相同),明顯地在程式是寫死的。
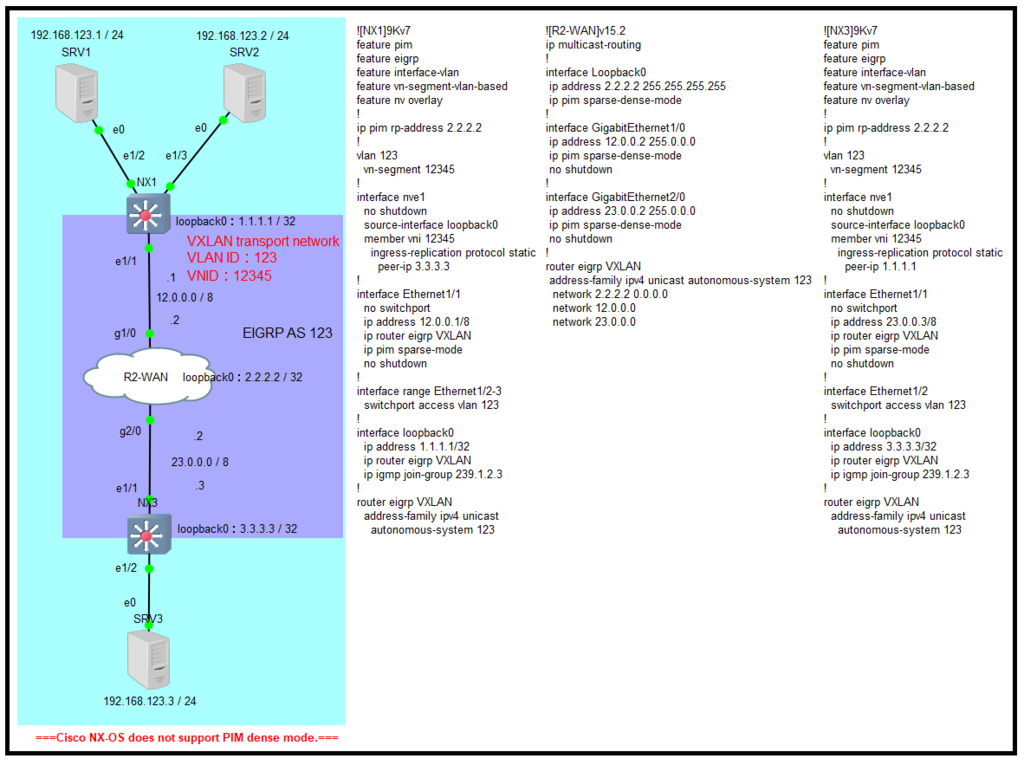
[整合HSRP & VXLAN的拓樸、配置]


需要注意的是,NX2與NX3都有直連網段23.0.0.0/8,如要將它通告給外部網路,只要擇一路由器做通告即可,筆者建議擇active路由器以方便管理,其他standby、speak路由器不通告23.0.0.0/8,但可以用Cisco EEM工具檢測自己是否成為active並通告23.0.0.0/8。小提醒,原生vlan不允許被擴充。
精彩的來了!如果QEMU-KVM的動態遷移技術透過HSRP & VXLAN的整合,實現廣域網路動態遷移呢?
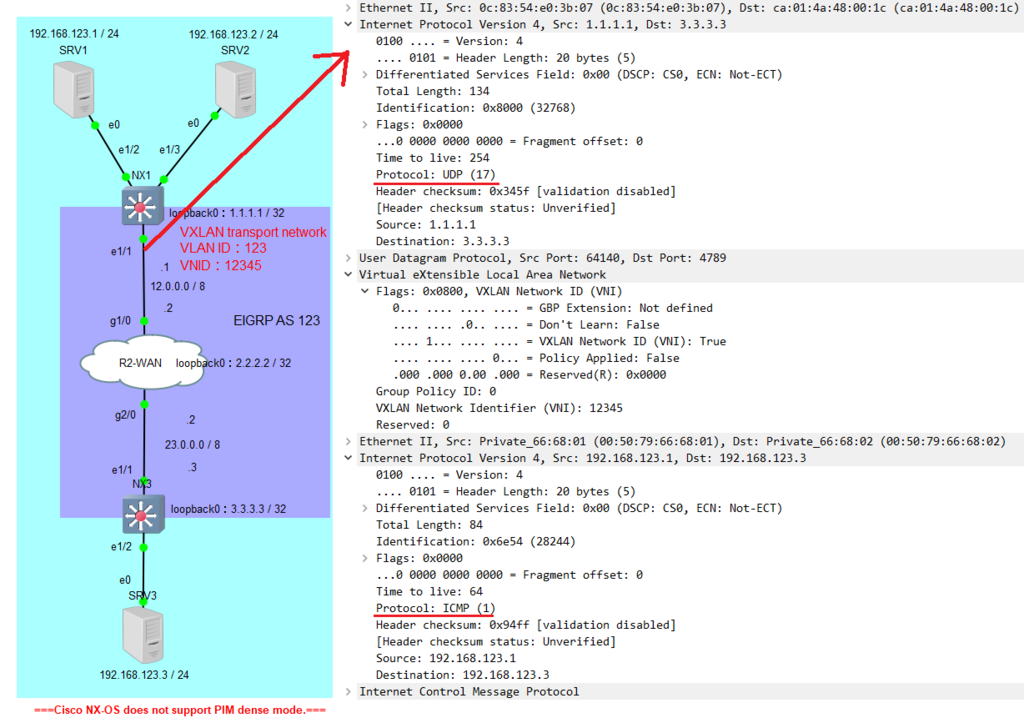
完全解決被遷移的guest OS的網路配置挑戰,無需更改IP設定,因為預設閘道的IP與MAC地址都指向HSRP路由器;也不用更改路由器上的NAT(如果有)。理論上ARP表的影響小,而MAC表需要時間收斂,因為它記錄MAC地址、從哪個介面學到。
若遷移前後的兩個網路不是相同網段則要留意IP環境,除非服務器使用IPv6 anycast,這允許多址做最佳 / 鄰近繞送。
然而有一問題尚未解決,原本2個直連的QEMU-KVM連線已經容易逾時,跨廣域網的連線更是一大挑戰。或許部署策略性QoS可以考慮,一旦產生遷移請求,基礎架構可以自動調整頻寬給特定的流量。
若有配置port-security也需特別留意,請注意!port-security address table與MAC address table是獨立的,儘管某主機之MAC地址已從交換器的MAC表移除(無論是因收斂 / 老化時間),但port-security表仍保存該MAC地址!這需要IT人為清理。原理請參考筆者先前的文「[Chin] Cisco IOS port-security安全漏洞」。
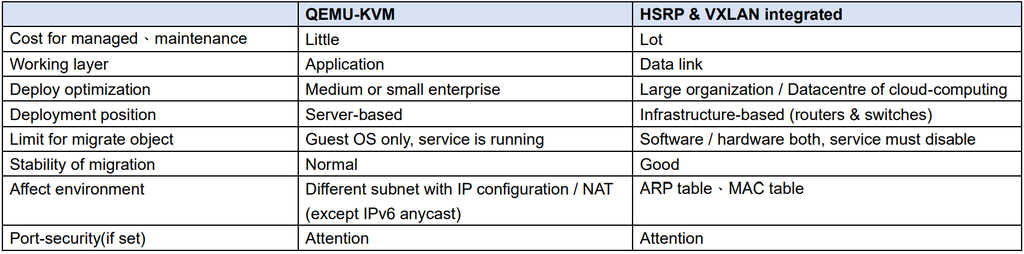
This writing is fit adVanced IT. First, we review these technologies for HSRP, VXLAN and virtualization. And list their features.
HSRP
It is gateway redundancy and developed by Cisco. Routers are join specific multicast address. On physical, there are multi-WAN to leave. On logical, one WAN for endpoint.
Usually, only one router that forward packet. Will Standby router take over forward priority when router of active dead. It desirable to minimize recovery time.
VXLAN
Although it is technology of L2. But it used UDP to implement extend VLAN. Application for infrastructure of large datacentre. To deploy VXLAN, it allow more datacentre use same subnet.
[Topology & configuration]
[image]
[Packet of VXLAN]
[image]
Live migration of virtualization
It is migration for running-host, and we still expect it is providing service or resource access. I introduce QEMU-KVM only, it is software of virtualization class. The simulate software such as Oracle vm virtualbox, VMware workstation player.
For common application, is virtual machine(s). In definition of term, your physical computer is host OS, your virtual computer is guest OS.
You can install diversified operating-system. It broken is not problem! Also for experiment, to test software, virus, system resource and so on.
For prepare migration, you need install QEMU-KVM on 2 computers. And to use hypervisor make container that install or import guest OS. For establish connection of QEMU-KVM.
[My host OS is mint18. Host OS and 10.1.1.18 are QEMU-KVM connection, and running guest OS that named vm]
[image]
GUI operate is simple, commands are follow
apt-get install qemu-kvm libvirt-bin ubuntu-vm-builder bridge-utils virt-manager python-spice-client-gtk qemu-utils spice-vdagent ssh
Install QEMU-KVM. The complement content, you can use 「apt-get install cpu-checker」 to install program of CPU checker, and use 「kvm-ok」 to detect does host OS support KVM?
virt-install --name vm --ram 1024 --vcpus 1 --cdrom /var/lib/libvirt/images/CorePlus-current.iso --disk /var/lib/libvirt/images/vm.qcow2,device=disk,bus=sata,format=qcow2,size=0.1
Install virtual machine and set parameter.
virsh [start / reboot / shutdown / destroy] vm
To start / reboot / shutdown / destroy for virtual machine.
virsh connect qemu+ssh://[username]@10.1.1.18/system
Prepare connection with peer. Connection mechanism of QEMU-KVM with used round-robin.
The migration has 3 conditions. (1) QEMU-KVM connection by SSH, it as tunnel not remote-login.
(2) For 2 peers, must exist same container name. The containers size can difference, but must with more than guest OS size.
(3) For 2 peers, their directories must same. If guest OS stored at /var/lib/libvirt/images/ of localhost, destination of migration also must same that /var/lib/libvirt/images/.
[Migrating guest OS]
[image]
The timing of migrating are network quality and guest OS size(it like transport file). The window of 「遷移虛擬機」 has a field of 「位址」, it can as hostname.
But you first to write some context for local name resolve file, file located /etc/hosts, or your DNS server can find it.
virsh migrate --persistent --undefinesource tiny qemu+ssh://[username]@10.1.1.18/system
To migrate guest OS to destination.
As above, is simple introduction with QEMU-KVM live migration. However, I felt it has some disadvantages. One is connection quality that bad, timed out easily.
Another is 3rd of migration condition.
[Topology with integrated HSRP & VXLAN, and configuration]
[image]
[image of CLI]
You need attention. NX2 and NX3 are have directly subnet of 23.0.0.0/8. If advertise to external network, can select one router only. I suggest select active router.
The standby, speak routers can use Cisco EEM tool that detect self be active router and advertise subnet with 23.0.0.0/8. Attention, native-vlan is not allow extend.
The wonderful coming! If live-migration technology of QEMU-KVM, integrated and HSRP & VXLAN, to deploy migrate over WAN?
It resolved network configuration of guest OS migrated perfectly. Because default gateway's IP and MAC address are directed HSRP router. Also not need change NAT configuration on router(if set). Theoretically, effect of ARP table is little. But MAC table needs some time that convergence.
Because it record MAC address, and learned from which interface. If before and after the migration that 2 networks are not same subnet, you need attention IP environment. Unless your server used IPv6 anycast, it allow multi-addresses doing best / nearest routing.
However, one more problem still exist. Originally, the 2 directly connected QEMU-KVM connection that timed out easily. So migration over WAN that is challenge. Maybe deploy QoS of policy. When migration request happened, infrastructure can auto adjust bandwidth for specific traffic.
If port-security configured, also attention. There are independent that port-security address table and MAC address table. Although MAC address of specified host that removed from switch(no matter convergence / aging). But port-security address table still record the MAC address!
It need clear table by IT. The principle that refer my writing for 「[Chin] Cisco IOS port-security安全漏洞」.




 留言列表
留言列表


