首先review一下Cisco的port-security功能,這個功能的本意是為了防止未受信任者擅自接線,甚至偷偷地將員工電腦上的網路線,拔下並插上自己的筆電。
從摘要的技術角度而言,原理是終端主機上網會透過預設閘道(路由器)出去,但是終端主機不知道區域網路上的閘道地址,於是送出ARP請求(廣播封包),無論區域網路是否存在其他節點,交換機都會紀錄該終端主機MAC地址從哪個端口進來。如下圖,區域網路為10.1.1.0 / 24,R1為預設閘道(.254),SW1為交換器,PC1為終端主機(.1);並在SW1的e0/2啟用port-security。
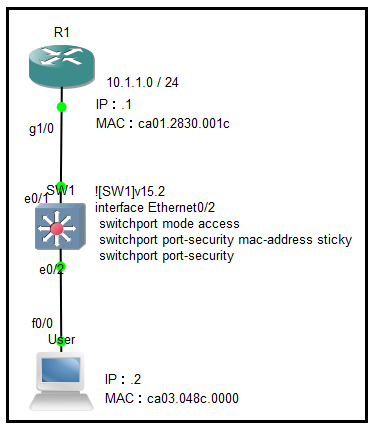

因為e0/1的port-security最大地址數為1,加上黏到了使用者的MAC地址;如有任何第二個MAC地址從e0/2進入,SW1會將端口e0/2關閉(預設行為),並只能由網管人員登入SW1,管理性關閉該端口、清除違規MAC地址、最後管理性啟動該端口。
在此就不贅述port-security的最大地址數、違規類型、違規行為等,或請查閱官方文件、CCNA。
然而,此功能也存在漏洞,這個漏洞通常有兩種情形:
1.使用者搬家。
譬如發生在大樓整修、辦公室裝潢,使用者從辦公室A遷移到辦公室B,並且使用者電腦的遷移前後位於相同廣播網域;這是小事,使用者僅反應無法上網。
2.偽造MAC地址
對高手而言要知道區域網路上任一台電腦的IP地址、MAC地址不是難事,甚至易如反掌。只要將攻擊者電腦的MAC地址修改為被攻擊者電腦的MAC地址,完成。
請參考下圖:


駭客配置了與區域網路相同網段的IP地址、並偽造被攻擊者的MAC地址,最後發任何廣播形式的封包,便形成某種MAC攻擊手段。
SW1收到駭客傳送的封包,都會認為這些資料是從e0/2進來的,因為這些資料的來源MAC地址都是ca03.048c.0000,使SW1會轉發這些資料經由e0/2。另外,port-security表是依賴在MAC表之上的。
此功能造成的最大影響只有極少數end-user,所以目前解決方案還是依照教材上的標準方法;如果您知道更好的方法,歡迎在下方留言告訴我。
First, we review function for Cisco port-security. The function wants prevent plug cable for untrusted user. Even, unplug cable from employee host and plug laptop self.
For brief, the principle is end-host that surfing Internet through default gateway(router). But host doesn't MAC address of gateway on LAN.
Thus, it sent ARP request(broadcast packet). No matter there are other nodes on LAN, switch has record MAC address of host which ingress port. As shown, LAN is 10.1.1.0 / 24, R1 is default gateway(.254), SW1 is switch, and PC1 is end-host(.1). And enable port-seucurity in SW1 e0/2.
[topology]
[show port-security, show mac address-table on SW1]
Because max secure address quantity is 1 for e0/2, and it had sticky MAC address of user. If any second MAC address originated from e0/2, SW1 will shutdown interface e0/2(default action).
The situation had by MIS login SW1 only, administrate disable the interface, clear violation for MAC address, last administrate to enable the interface.
I don't repeat them here that port-security for max address quantity, violation action and so on. You can look up official doc, or CCNA.
However, the function has bug. There are two situation generally:
1. User migration.
Such as building renovation, office decoration. User migration to office B from office A. The office A and B are located same broadcast domain.
It is fig. The user will react doesn't surfing Internet.
2. Forged MAC address.
For master, if it want to know any host on LAN for IP address, MAC address, is not difficult. You have change MAC address to be attacked host, finish.
As shown:
[topology]
[show running-config interface f0/0, ping 10.1.1.255 in Hacker]
Hacker has set IP address of the same same network as LAN, and forged MAC address for be attacked. Last, hacker sends any broadcast packet that perform some MAC attack method.
SW1 receive packets from hacker, it think these data are ingress from e0/2. Because these data that source MAC address are ca03.048c.0000 . It cause SW1 has forward the data to e0/2. Additionally, port-security table is rely MAC address table.
The function cause max effect that a few end-user only. So the solution is follow standard method on book currently. If you know better methods, welcome leave message below for me.




 留言列表
留言列表


